Update: 15 October 2025
GreyNoise is sharing an Executive Situation Report (SITREP) for this event, providing leadership with actionable judgments and evidence to support decision making.
Update: 14 October 2025
In a significant escalation, the botnet has grown to ~300,000 IPs — more than tripling in size. The threat actor(s) continues its focus on RDP infrastructure in the United States, leveraging IPs from Brazil, Argentina, Singapore, and other countries.
The associated threat actor(s) is rapidly activating new botnet nodes to target U.S. RDP infrastructure. Therefore, static defense measures will not be effective at mitigating this threat.
Since October 8, 2025, GreyNoise has tracked a coordinated botnet operation involving over 100,000 unique IP addresses from more than 100 countries targeting Remote Desktop Protocol (RDP) services in the United States. The campaign employs two specific attack vectors — RD Web Access timing attacks and RDP web client login enumeration — with most participating IPs sharing one similar TCP fingerprint, indicating centralized control.
Use GreyNoise Block to dynamically block all IPs engaged in this activity. New users can try GreyNoise Block free for 14-days.
- Leverage the template named “Oct-2025 RDP Botnet Campaign"
Key Findings
- Campaign start: October 8, 2025 — coordinated RDP targeting wave begins.
- Scale: Over 100,000 unique IPs participating in US-focused RDP attacks.
- Geographic scope: 100+ source countries including Brazil, Argentina, Iran, China, Mexico, Russia, South Africa, Ecuador, and others.
- Primary target: United States RDP infrastructure, mostly uniform across source countries.
- Attack methods: Microsoft RD Web Access Anonymous Authentication Timing Attack Scanner and Microsoft RDP Web Client Login Enumeration Check.
- Signatures: Similar TCP fingerprints across all participating IPs. GreyNoise customers can check their email for the precise client signatures identified.
- Botnet activity: We assess with high confidence that the elevated RDP targeting beginning this week is attributable to a multi-country botnet.
Discovery Timeline
Spike in Brazil-geolocated IPs
The botnet was discovered after GreyNoise detected an unusual spike in Brazilian IP space this week, which prompted investigation into broader traffic patterns.
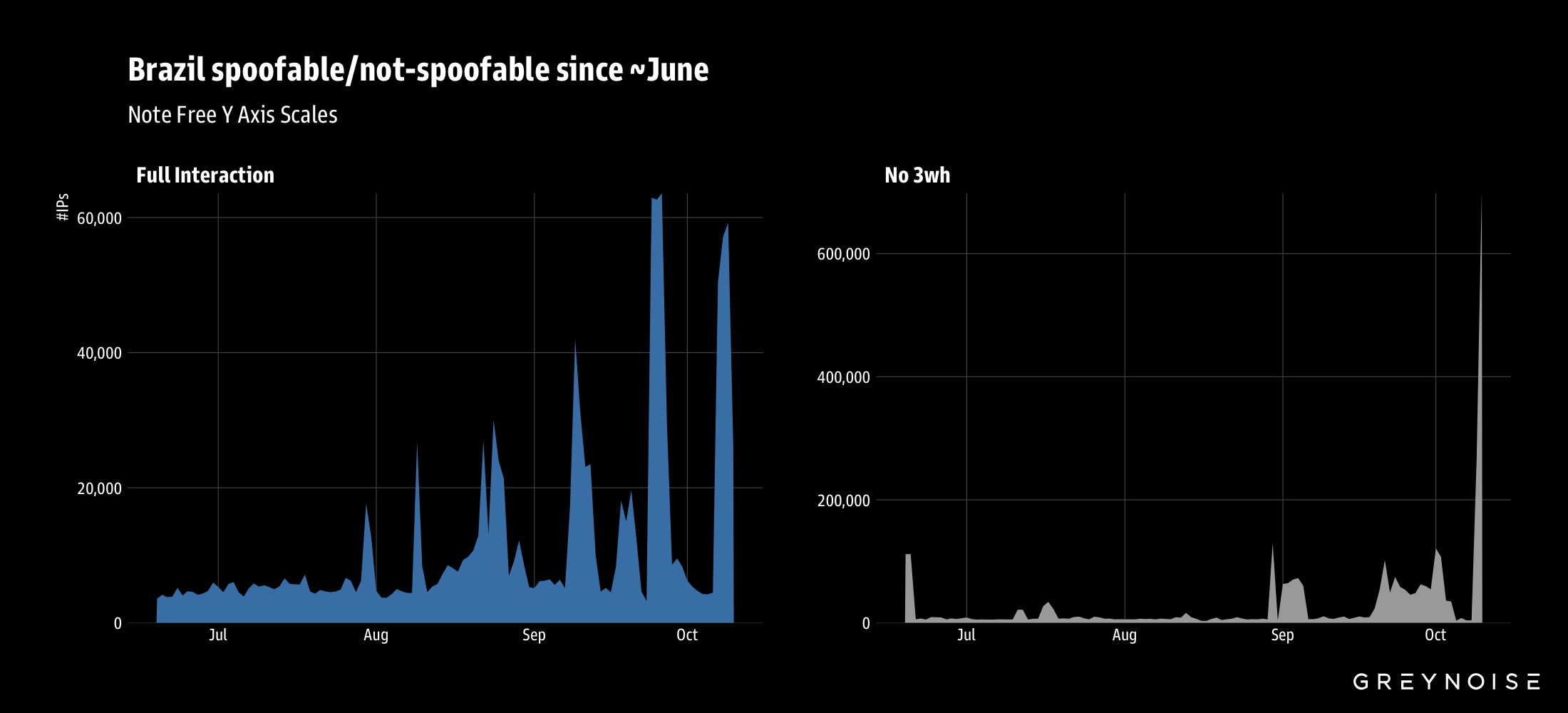
Note: Full interaction = completed three-way handshake; No 3wh = no three-way handshake
Broader Spikes Across Source Countries
Broadening our analysis, we observed additional surges in activity across many source countries since the beginning of October.
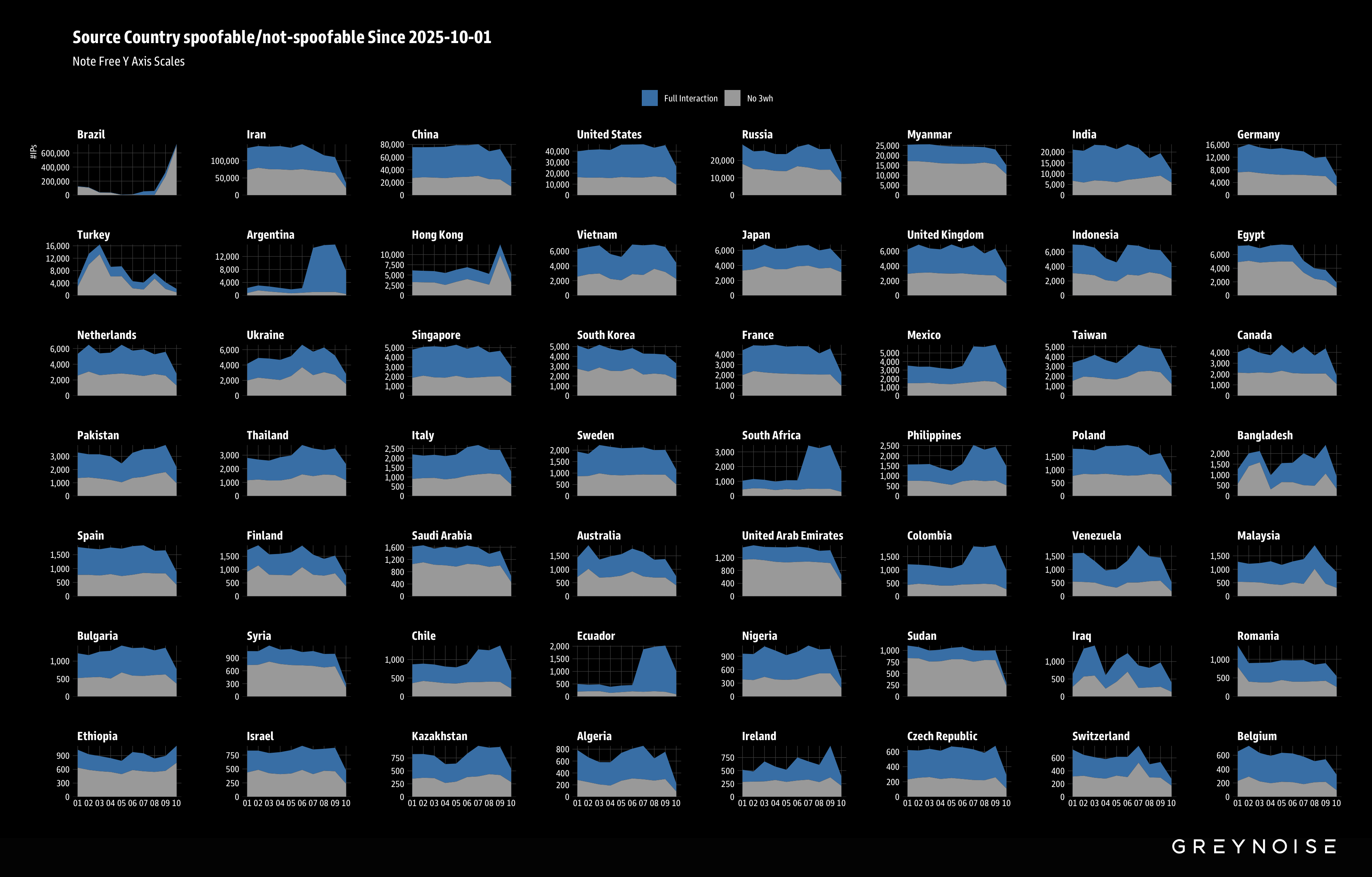
Multi-Country Botnet Targeting US RDP Infrastructure
Pivoting from these findings, we then discovered a repeated pattern in RDP targeting — originating from many countries, sharing a similar client fingerprint, and all targeting US RDP infrastructure.
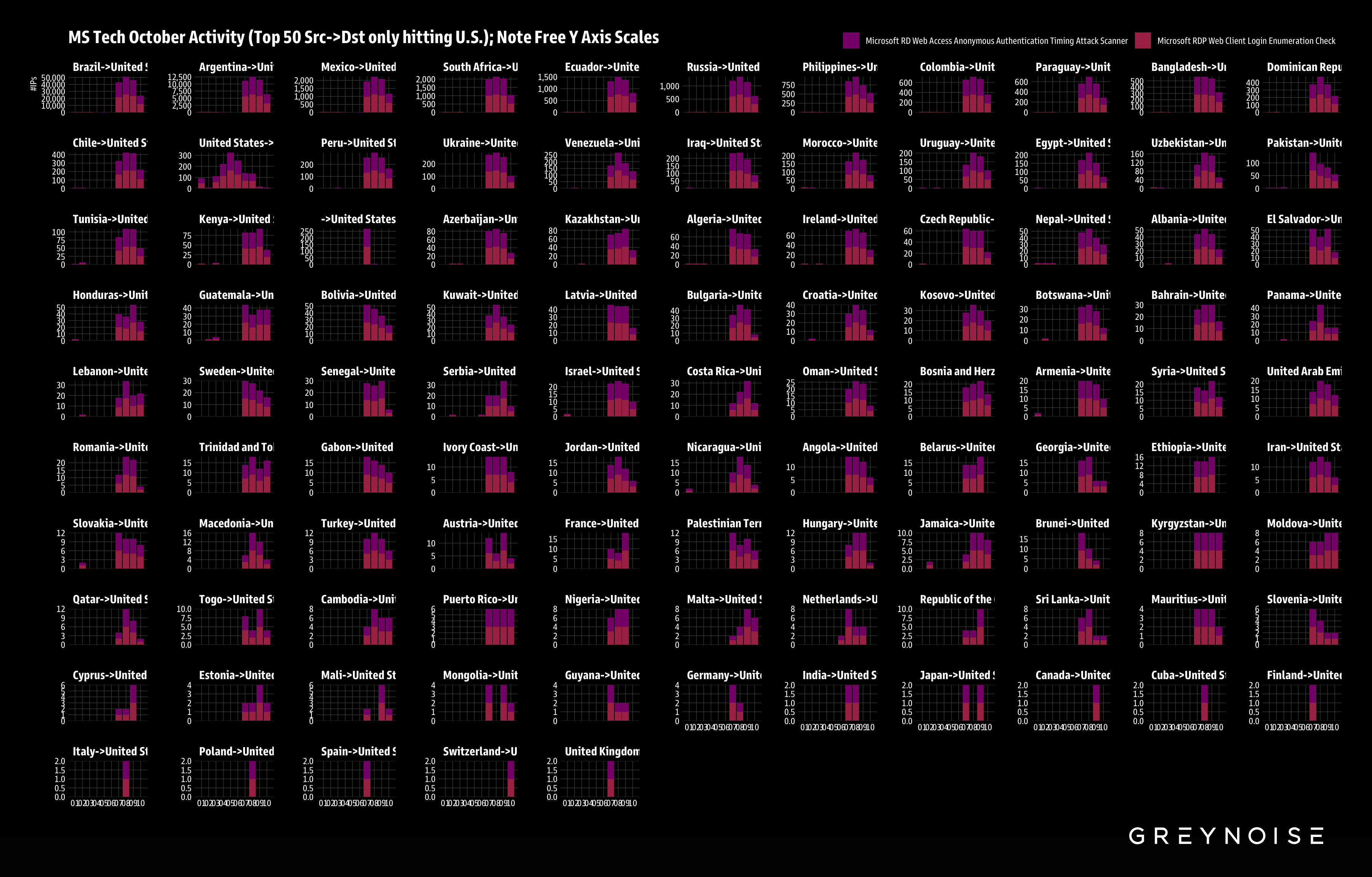
Several factors suggest this activity is originating from one botnet:
- Almost all traffic shared one similar TCP fingerprint, with only the MSS changing.
- MSS in this context likely changes depending on the compromised botnet cluster.
- The timing and pattern of targeting implies coordinated activity with centralized control.
- The shared RDP attack vector again suggests centralized control, likely activated by the operator(s) for this sole purpose.
Defender Recommendations
- Use GreyNoise Block to dynamically block all IPs engaged in this activity. Get started with a free 14-day trial.
- Leverage the template named “Oct-2025 RDP Botnet Campaign”
- Check logs for any unusual RDP probing.
- Monitor the GreyNoise tags implicated in this event:
GreyNoise will continue monitoring the situation and provide updates here as necessary.
---
This discovery was led by boB Rudis with contributions from the broader GreyNoise team.







.png)

.png)

.png)