
At GreyNoise, when we talk about honeypots, we sometimes get questions about honeytokens and how they differ. This may come from some of the great contributors to this space, making things like honeytokens widely available to experiment with (yay!). Setting up and deploying realistic and diversified honeypots is trickier, but there are still great contributors in closed and open-source projects.
Despite each's similar purpose of early threat detection, honeypots and honeytokens vastly differ in deployment, interaction, and scope. Let's delve into the various aspects contributing to the misunderstanding and clarify the distinctive features of each.
The concept of a honeypot as a security tool emerged in the early 1990s. Initially, honeypots were used mainly for detecting attackers in networks. The first honeypots were simple to fingerprint as they were fundamentally traps that were easy for experienced hackers to recognize and avoid.
In 1998, Fred Cohen, a renowned computer scientist credited with introducing the term "computer virus," developed and released the Deception Toolkit. This was a basic honeypot tool designed to mimic vulnerabilities, giving the appearance of a vulnerable system.
The term "honeytoken'' originated from a mailing list in 2003 and is credited to Augusto Paes de Barros. In a discourse with Lance Spitzner, founder of the Honeynet project, Paes de Barros discussed the possibility of expanding detection to articles such as accounts, documents, info, etc.

Now let’s take a look at a little more about each individually.
What is a Honeypot? A honeypot is a security tool designed to mimic vulnerable systems with the intent to attract attackers. The goal is to analyze attacker activities and methodologies, which can include things like identifying if critical vulnerabilities are currently being exploited in the wild.
Emulation and Monitoring: Honeypots are deployed as bogus systems or networks, luring attackers into a controlled environment where their actions are monitored, providing deep insights into their strategies and tactics.
Network-Centric: Honeypots, focusing predominantly on network or system levels, adeptly detect diverse attacks, including unauthorized access and exploitation.
What is a Honeytoken? A honeytoken is a decoy entity seamlessly blended into a system or data. Any interaction with a honeytoken is a clear indication of unauthorized access, promptly alerting organizations to potential breaches. It can be as simple as phony credentials to deceptive database entries. Various forms of honeytokens fortify systems against unauthorized infiltrations.
Seamless Integration and Alert: Honeytokens, embedded within data or systems, act as silent sentinels, triggering alerts upon unauthorized access, without any interaction with the attacker.
Data-Centric: Positioned at the data or information level, honeytokens adeptly detect illicit data access and insider threats.
While honeypots provide a more robust surface for attackers to interface with, thus providing extensive insights into attacker strategies, honeytokens silently monitor and alert organizations to unauthorized data interactions.
Honeypots primarily emphasize network or system-level security, whereas honeytokens accentuate data-level protection, guarding against unauthorized access and breaches.
In the mosaic of cybersecurity, honeypots, and honeytokens emerge as complementary, not competing, technologies. Honeypots, with their interactive and comprehensive insight into attacker behavior, coupled with the silent and alert-focused honeytokens, create a robust, multi-layered defense strategy. Organizations leveraging both are poised to significantly enhance their cybersecurity posture, staying ahead in the perpetual battle against cyber adversaries.
The intertwined utilization of honeypots and honeytokens reflects the evolving dynamism and complexity of cybersecurity, reinforcing the need for diverse, innovative, and integrated defense strategies to navigate the challenging cyber terrain effectively.
Want to learn more? Sign up for a free GreyNoise account to explore real data captured across our extensive network of honeypots.


Our new hosted sensor fleet is cranking out PCAPs for those lucky folks who made it into the first round of our Early Access Program. These sensors enable you to give up a precious, internet-facing IPv4 address and have it automgically wired up to your choice of persona. These personas can be anything from a Cisco device, to a camera, and anything in between.
While there’s a fancy “PCAP analyzer” feature “coming soon” to the GN Visualizer and API, I’ve been mostly using a sensor that’s tucked away in a fairly quiescent part of the internet to quickly triage HTTP requests to see if we can bulk up our Tag (i.e., an attack/activity detection rule) corpus with things we may have missed in the sea of traffic we collect, tag, and triage every day.
Sure, Sift helps quite a bit with identifying truly horrific things, but occasionally a quick human pass at HTTP paths, headers, and POST bodies will either identify something we may have previously missed, or cause us to think a bit differently and start identifying more of the noise. This is how our recent “security.txt scanner 🏷️” and robots.txt scanner 🏷️ were birthed.
We've posted a detailed write-up on one way to do this over on the GreyNoise Labs Grimoire. Check it out and share your analyses or alternate ways you processes thse PCAPs in the Community Slack!

Citrix's NetScaler ADC and NetScaler Gateway have, once more, been found to have multiple vulnerabilities, tracked as CVE-2023-4966 and CVE-2023-4967.
On October 23, 2023, GreyNoise Detection Engineers added tag coverage for CVE-2023-4966, which is an information disclosure vulnerability in NetScaler ADC and NetScaler Gateway. When configured as a gateway (VPN virtual server, ICA Proxy, CVPN, RDP Proxy) or as an AAA virtual server, an unauthenticated attacker could exploit the device in order to hijack an existing authenticated session. Depending on the permissions of the account they have hijacked, this could allow the attacker to gain additional access within a target environment and collect other account credentials.
CVE-2023-4967 is a denial-of-service (DoS) vulnerability that can potentially enable DoS attacks on vulnerable devices.
Both CVEs were published on October 10, 2023, and the tag for CVE-2023-4966 joins 11 other Citrix-specific tags in the GreyNoise tag corpus.
The GreyNoise Storm⚡Watch webcast/podcast provided extensive coverage of this vulnerability in this week’s episode.
As of this post’s publish time, GreyNoise has observed just under seventy IP addresses attempting to exploit this vulnerability:

Activity started on the 24th and shows no signs of stopping.

Citrix has urged customers to install updated versions of the affected devices as soon as possible. The recommended versions to upgrade to are NetScaler ADC and NetScaler Gateway 14.1-8.50 and later, NetScaler ADC and NetScaler Gateway 13.1-49.15 and later releases of 13.1, NetScaler ADC and NetScaler Gateway 13.0-92.19 and later releases of 13.0, NetScaler ADC 13.1-FIPS 13.1-37.164 and later releases of 13.1-FIPS, NetScaler ADC 12.1-FIPS 12.1-55.300 and later releases of 12.1-FIPS, and NetScaler ADC 12.1-NDcPP 12.1-55.300 and later releases of 12.1-NDcPP.
Citrix has provided no mitigation tips or workarounds at this time. Organizations are urged to patch immediately. The Cybersecurity and Infrastructure Security Agency (CISA) has added an entry for CVE-2023-4966 to its Known Exploited and Vulnerabilities Catalog, which contains detection and mitigation guidance for observed exploitations of CVE-2023-4966 by threat actors against NetScaler ADC and NetScaler Gateway.
Remote access technologies are prime targets for attackers, especially when proof-of-concept code becomes available. GreyNoise Detection Engineers work with research partners, and conducts bespoke vulnerability research to provide timely access to real-time intelligence that can help your organization buy time to patch, remove the noise of opportunistic attackers, and give you the opportunity to focus on fending off targeted attacks.

Cisco Talos has updated their advisory to include a new CVE, CVE-2023-20273, "that is exploited to deploy the implant" with a fix estimated to be released on October 22nd. The Cisco Security Advisory was also updated to include the new CVE, information about observed attacks, mitigation, and Snort rule IDs.
We have also updated our illustration (below) to include the new CVE.

On October 16th, 2023, Cisco disclosed a critical software Web UI Privilege Escalation Vulnerability under the identifier CVE-2023-20198 with a CVSS base score of 10. Cisco notes that the vulnerability has been exploited in the wild. The vulnerability allows an unauthenticated attacker to create an account with “privilege level 15 access” (full access to all commands). There is no patch for the privilege escalation vulnerability at the time of writing.
In coordination with this disclosure, Cisco Talos published a threat advisory noting that the privilege escalation vulnerability CVE-2023-20198 is leveraged for initial access. Following this activity, an implant is delivered through a “yet undetermined mechanism” for which no patch is available.
“Leveraging existing detections, we observed the actor exploiting CVE-2021-1435, for which Cisco provided a patch in 2021, to install the implant after gaining access to the device. We have also seen devices fully patched against CVE-2021-1435 getting the implant successfully installed through an as-of-yet undetermined mechanism.”
Later in the threat advisory, the Snort intrusion detection system rule ID 3:50118:2 is called out as a way to address “this” threat.
The Snort rule 3:50118:2 "SERVER-WEBAPP Cisco IOS XE Web UI command injection attempt” does not include any mention that it detects CVE-2021-1435. In the rule’s references section, CVE-2019-12650 and CVE-2019-1862 — both command injection vulnerabilities — are mentioned via the following links:
Though not explicitly called out as part of the Snort rule, CVE-2021-1435 is also a command injection vulnerability.
If Snort rule 3:50118:2 detects the command injection vulnerabilities (CVE-2019-1862 / CVE-2019-12650 / CVE-2021-1435?) and the malicious implant in this recent string of attacks is installed through a “yet undetermined mechanism” on systems that are fully patched against CVE-2021-1435, then the vulnerability being leveraged to install the implant is not CVE-2021-1435. Additionally, a patch is available for CVE-2021-1435 whereas a patch is not available for the mechanism used to install the implant.
.png)
Further research by VulnCheck has demonstrated that systems affected by the malicious implants can be coerced to disclose their 18-character hexadecimal unique implant identifier.
Cisco buried the lede by not mentioning thousands of internet-facing IOS XE systems have been implanted. VulnCheck scanned internet-facing Cisco IOS XE web interfaces and found thousands of implanted hosts. This is a bad situation, as privileged access on the IOS XE likely allows attackers to monitor network traffic, pivot into protected networks, and perform any number of man-in-the-middle attacks.

Censys also configured a scan profile and published their results in a blog post. It’s not a pretty picture. Over 40K Cisco IOS devices had their web admin interfaces exposed to the internet and fell victim to the latest round of implant attacks.
More distressing is that some of these devices are being used to launch further attacks. Researchers from both VulnCheck and Censys were kind enough to run their results through the GreyNoise Analyzer, which enables bulk triage of IP lists. Over 120 devices have been put into malicious service by attackers and live in diverse autonomous systems:
Unsurprisingly, we’re also seeing a large uptick in scanning from malicious, benign, and “unknown” sources in our Cisco IOS XE CVE-2023-20198 Scanner tag:

A key aspect of the current, underlying implant is that it does not survive a reboot. That means attackers will need to reinfect devices in their control if power is cycled or if they perform regular maintenance that requires a reboot… unless they have created a persistent access method prior to the reboot such as a newly created account. Given that these Cisco appliances are (small) business-class devices, they are more likely to have static IP addresses, meaning that attackers won’t have to re-scan the entire internet nearly as often as they might otherwise to identify and re-infect them.
Censys, VulnCheck, and GreyNoise can only report the view from the outside. However, similar Cisco IOS devices are also used internally in many organizations and are equally susceptible to this vulnerability. After gaining initial access on a low-privileged endpoint, attackers will no doubt be probing for vulnerable Cisco devices internally, where it is even more likely the web admin UI will be enabled. Having such privileged access to an internal router/network may be even more valuable/desirable than internet-facing ones.
Researchers from GreyNoise Labs strongly encourage organizations to disable the HTTP Server feature on all internet-facing systems until a patch is available (and consider leaving it disabled permanently). This can be done by following the instructions provided in the Cisco security advisory.
Given the transient nature of the implant, they also suggest conducting an incident response exercise to determine if any internet-facing (or internal) Cisco device was demonstrating anomalous behavior.
Remember, you can:
GreyNoise Labs will continue monitoring this situation and providing updates as needed.
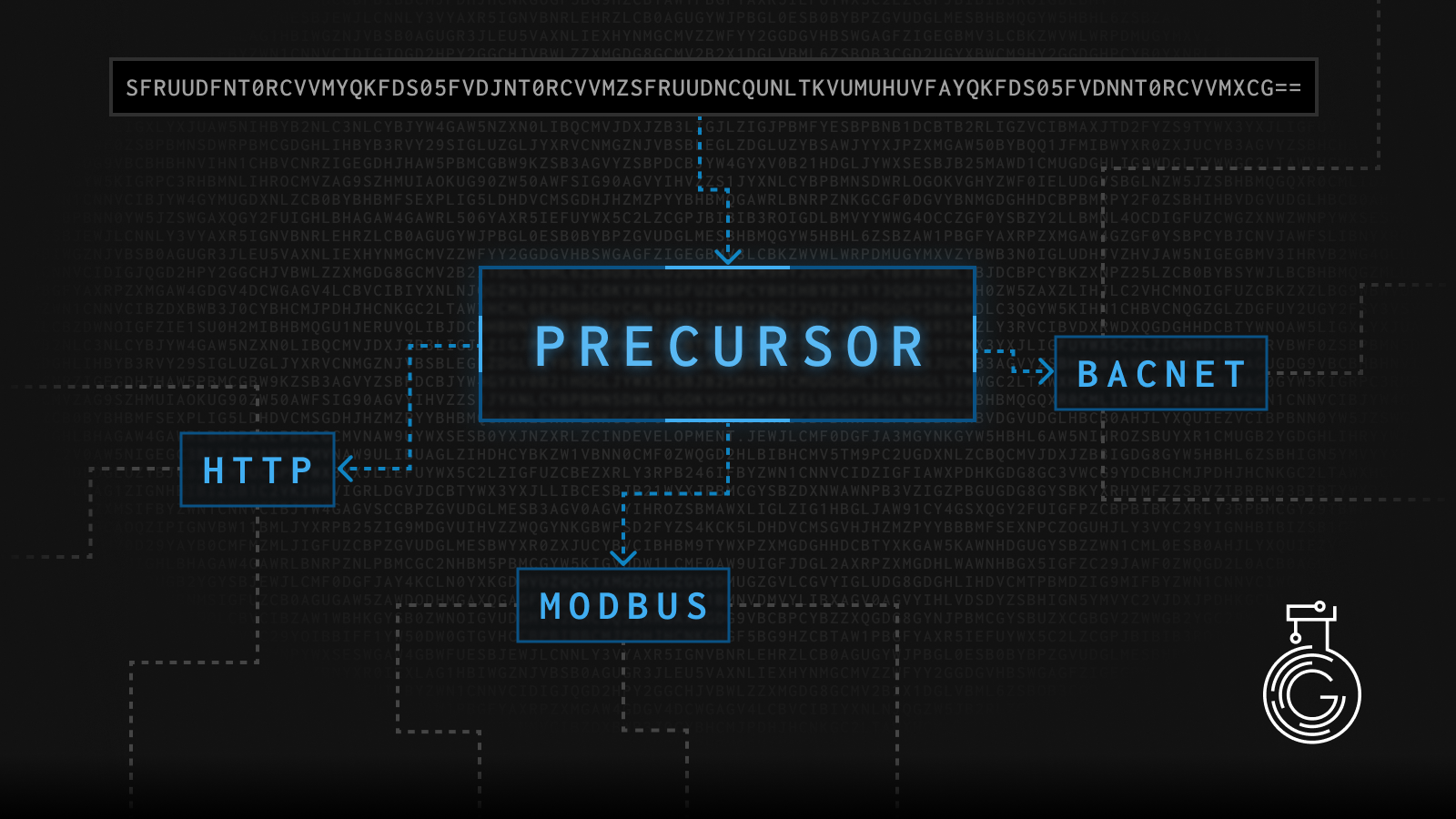
Precursor: A Quantum Leap in Arbitrary Payload Similarity Analysis
In both general “data science” and, especially, in many cybersecurity contexts, the ability to identify and analyze similarities in data is crucial. Matt Lehman, from the GreyNoise Labs research team, has a new, deep-dive blog post introducing a new tool — Precursor — which promises to revolutionize how we approach this task. It is designed to label and find similarities in text, hex, or base64 encoded data and is a product of extensive research and development.
Precursor supports arbitrary similarity algorithms that generate a digest and support distance calculations, such as MRSHv2 and SSDEEP. It also provides a generic similarity vector output that machine learning processes can ingest. Precursor’s binary input mode for firmware/malware analysis can automate including the protocol indicators from existing libraries into PCRE2 patterns where applicable. The tool also supports a training mode where it can automatically configure the optimal similarity algorithm and distance thresholds.
Potential other use-cases include:
Threat Intelligence and Attribution: Precursor can be used to analyze network traffic and identify patterns that indicate a potential threat. For instance, it can help in identifying regionally targeted cyberattacks by analyzing the nature of the traffic targeting a specific region. This was demonstrated when GreyNoise used Precursor to analyze a cyberattack targeting Israel.
Malware Analysis and Detection: Precursor's ability to support arbitrary similarity algorithms can be used to detect malware. By comparing a suspicious file to a database of known malware signatures, Precursor can help identify whether the file is malicious. It can aid in detecting command and control (C2) communications often used by malware.
Network Traffic Analysis: Precursor can be used to analyze network traffic and identify patterns or anomalies that may indicate a security threat. For instance, it can help in identifying scanning and enumeration activities typically associated with the reconnaissance phase of a cyberattack.
Stay tuned as we delve deeper into the workings of Precursor, its potential applications, and the insights it has helped us uncover. Whether you're a cybersecurity professional, a data scientist, or simply a tech enthusiast, this tool is set to bring a new level of sophistication to your work.

On October 11th, 2023, a heap-based buffer overflow in curl was disclosed under the identifier CVE-2023-38545. The vulnerability affects libcurl 7.69.0 to and including 8.3.0. Vulnerable versions of libcurl may be embedded in existing applications. However, to reach the vulnerable code path, the application must be configured to utilize one of the SOCKS5 proxy modes and attempt to resolve a hostname with extraneous length.

In a controlled environment, reproducing the bug itself is trivial. Pictured below is a vulnerable version of curl requesting a hostname consisting of 10,000 A’s through a configured SOCKS5 proxy, resulting in memory corruption leading to a Segmentation fault.

In practice, the scope of the vulnerability is more nuanced. As noted above, curl must be configured to utilize a SOCK5 proxy to reach the vulnerable code path. If you run an application utilizing a vulnerable version of curl/libcurl that makes HTTP requests and an attacker can set the “http_proxy” environment variable, curl may automatically inherit that configuration, allowing the vulnerable code path to be reached (pictured below). Of course, this assumes that the attacker already has some level of privileged access to set these environment variables. At such a point that an attacker already has privileged access, leveraging this curl vulnerability is certainly not the easiest path to remote code execution.
.png)
Through the lens of “exploit-ability” in practical deployments of curl, few could be remotely triggered. After significant research, the GreyNoise Labs team was able to identify one such configuration scenario that we would be able to track and have created a tag for detecting it. In the unlikely event that more vulnerable-in-practice applications come to light in the coming days, the tag will be updated to capture the associated traffic.

A critical zero-day vulnerability has recently been discovered in the Confluence Data Center and Server.
The vulnerability, known as CVE-2023-22515 and scored a CVSS 10 out of 10, is a privilege escalation vulnerability that allows external attackers to exploit the system and create administrator accounts that can be used to access Confluence instances.

Atlassian, the company that produces Confluence, rates this vulnerability as 'critical' and has released patches for it. On-premise instances of Confluence on the public internet are at risk as this vulnerability is exploitable anonymously. Atlassian has stated that cloud-hosted versions of Confluence are not impacted, but it is unclear if they were vulnerable before the patch. Atlassian also has published an FAQ for this vulnerability.
We recommend immediately upgrading to the latest patched version, especially if you use an exposed or internet-facing Confluence instance. Since exploitation was observed before the advisory and patch were issued, organizations should audit user accounts and signs of compromise. As a standard practice, you should also restrict network access to any Confluence instance.
GreyNoise has published a tag monitoring for CVE-2023-22515 exploitation attempts.
If you’re curious about viewing scanning activity related to the “/setup/setupadministrator.action” web path, you can view that here; and if you’re curious about IPs that are searching for any ”setup*.action” web paths, you can view that here.

GreyNoise is exposing a new internally developed tool, Sift, to the public for the first time. Sift curates a report of new/interesting traffic observed by GreyNoise sensors daily after doing much of the analysis and triage work itself. Check it out at https://sift.labs.greynoise.io/
Note that it is a new and experimental feature and will probably have some bugs and change without warning. We will soon be integrating direct marker.io feedback capability. For now, please direct all feedback to labs@greynoise.io. We really want to know what you think!

There is a lot of traffic bouncing around the internet. Full stop. GreyNoise sees ~2 million HTTP requests (along with tens of millions of events from other protocols) a day. For our on-staff Detection Engineers and your engineers and analysts facing similar loads, analyzing millions of HTTP requests can be extremely tiresome and stressful.
It’s like looking for a needle in a haystack each day. Most of them are harmless, but some could be hiding malicious activity. It’s a tedious and time-consuming process, constantly payloads of data, and the fear of overlooking something dangerous adds a layer of stress. The task is mentally exhausting, and the perpetual strain can make it a painful experience, with the constant awareness that a single mistake could have serious consequences.
To help provide a painkiller, we’ve created Sift. Sift is a workflow that attempts to remove the noise of the background traffic and expose new and relevant traffic. Additionally, it describes the interesting traffic, tells you if it might be a threat, and prioritizes what payloads to look at first. Identification, explanation, and triage all in one tool.
To achieve this, we employ several advanced DS/ML/AI techniques, such as:
The result is a daily report of what GreyNoise sees in our vast sensor network distilled down to only the new items and with built-in analysis to give every defender an immediate look into what is really happening on the internet, no longer needing the luck of an analyst stumbling upon an attack in log traffic.
Currently, it is limited to HTTP traffic, but that won’t last long. It is an experimental feature on the bleeding edge of what is possible, so please bear with us as errors inevitably occur.
As said earlier, GreyNoise sees millions of HTTP requests a day. After months of experimentation, we found several techniques to record, clean, dedupe, and convert this data into a numerical format for analysis. Applying this to our significant dataset of internet traffic, we’re able to automatically tell you what is new today vs. what we have seen in the last several weeks. This process effectively makes a noise filter for traffic.
In practice, our process takes ~2 million HTTP events down to ~50 per day that require an analyst to look at. Now, we can actually find the needles in our proverbial haystack scientifically and give our analysts a reasonable workload. This reduction in noise has dramatically improved the quantity of new Tags we can generate every week.
Once we’ve narrowed our focus, we can employ some of the more costly techniques of commercial large language models to help us answer specific questions about the payloads we’re considering. Without giving away all our techniques of how we accomplish it, we can generate an analysis of the payload, potential CVEs, and CPEs associated (which are more up-to-date than any language model), a score of how big of a threat it might be, what GreyNoise knows about the IPs (tags/riot/etc), a score of how confident we are, Suricata queries that might detect similar payloads, as well as keywords, techniques, and technologies affected.
In short, we’re trying to build an entire analyst report on the fly for only things you should look at. Additionally, we sort the reports, so you look at the most critical threats first.
Sift is brand new and full of possibilities. You can help flesh those out. We’re currently only exposing daily reports from the last month (excluding the previous week).

As autumn quickly approaches in the Northern Hemisphere, many people see this as a time to turn inward and prepare for the long winter ahead. However, this is also a time when the lush, uniform green flora around us transforms into a kaleidoscope of colors. This change helps give us all a renewed perspective on what is all around us and fuels both an appreciation for what we have and creativity for what is possible.
Today, GreyNoise is excited to officially announce the emergence of GreyNoise Labs. Keen-eyed GreyNoise users may have noticed our soft launch of this throughout 2023. Back in June, Kimber Duke announced our Labs APIs to the world. The Labs API is a powerful tool designed to provide users quick access to existing and new data we collect and process at GreyNoise via an early access/beta API experience.
Now, like the autumn leaves, we're adding even more color to the existing knowledge and insight that GreyNoise already provides, which governments, critical infrastructure, Fortune 100 enterprises, and security researchers rely on daily to help defend us all against cyberattacks.
You already know one of our goals: to provide early access to new data, tools, and insights we're developing — things that may eventually become integrated into our core product but need testing, feedback, and real-world use.
All the teams at GreyNoise provide product, company, community, and emerging threat information via our primary communication channel. This is still the place to keep your finger on the pulse of what's happening at GreyNoise and in the internet threat landscape. If our GreyNoise blog's RSS feed still needs to be added to your favorite newsreader, we highly recommend adding it right now!
That is still the place where critical, actionable information associated with emerging threats will first be published. However, we often need to go deeper into a particular vulnerability or exploit. We also have much more to say on security research projects we're undertaking, data science initiatives we're investigating, and cutting-edge detection engineering concepts we're pioneering.
Our new Grimoire blog (Grimoire RSS) is the place for these deeper dives. We'll make sure to link to them if we have more to say about any emerging threats we direct your attention to on the core blog.

The GreyNoise Labs API is part of our internal Blueprints initiative. Our Product, Design, and Engineering teams build, maintain, and enhance resilient and robust systems/applications you rely on daily. Our Labs team is charged with developing new ways to process and present the data we collect, curate, and compute. These ideas are codified into "blueprints," which are — by definition – "something intended as a guide for making something else." These may take the form of a new Labs API or greynoiselabs command line endpoint, alternate ways to view our data, different idioms for interacting with our core services, or just ways to help you see how we think about the data we work with.
We'll also be regularly updating resources we rely on and giving folks a bit more insight into the team behind GreyNoise Labs. Curious about what we do, what we've published, or the APIs we've made available? Drop us a note at labs@greynoise.io.

When it comes to threat intelligence and security operations automation, managed security service providers (MSSPs) face some pretty unique challenges. In our recent webinar, we had the pleasure of hosting two MSSP leaders, Alan Jones and Corey Bussard, who shared their own automation journey. They talked about the hurdles they encountered at the beginning, the value automation brought to the table, and how it has impacted the human element of cybersecurity. Let's dive right in.
One of the biggest challenges is the overwhelming number of alerts generated by various security tools. A significant portion of this alert noise originates from inadequate or improperly adjusted threat intelligence feeds. Instead of offering valuable context, many threat intel feeds end up exacerbating false positives and increasing the workload for analysts. Because MSSPs manage a large number of clients, this challenge is amplified compared to your average company.
In order to overcome the overwhelming amount of noise, these MSSPs recognized the need for improved threat intelligence sources to validate alerts, as well as workflow automation. By validating threat intelligence from trusted providers like GreyNoise, they were able to effectively reduce false positives by swiftly eliminating non-malicious alerts. The implementation of automation for these repetitive analyst tasks and interactions with security tools resulted in a significant boost in overall efficiency.
By combining automation with high-fidelity threat intelligence, these MSSPs were able to streamline their operations and empower their analysts to focus on the most critical threats.
A big thank you goes out to Alan and Corey for graciously sharing their automation journey. They did an exceptional job of explaining the immense value of automation, as well as underscoring the crucial role that the human element plays in their success. We highly encourage you to watch the full webinar on-demand and gain valuable insights from these industry leaders.
.png)
Introducing the GreyNoise Labs Python CLI package: a robust toolkit for advanced users seeking to maximize the potential of our experimental Labs services.
Cybersecurity data analysis is a complex and rapidly evolving landscape. To stay ahead, power users need tools that offer swift and accurate data handling. That's where the new GreyNoise Labs CLI package comes in. Crafted to optimize the parsing and manipulation of our sensor datasets, this CLI will not only expedite your process but also deliver digestible insights right at your fingertips.
The package serves as a conduit to the GreyNoise Labs API service, facilitating direct access to raw sensor data, contextual metadata, and quick prototyping utilities. This powerful Python package is your key to unlocking a simpler, more efficient interaction with our Labs API.
The GreyNoise Labs API contains the top 1% of data for all queries. However, the fluid nature of our continuous iteration and experimentation means that queries and commands can change without prior notice, and a rate limit is in place for equitable usage. While these utilities are primarily intended for us to explore new concepts and gather valuable user feedback, you're welcome to use them. We do caution against integrating them directly into production tools.
Our objective is to identify and prioritize new product features through these experimental iterations and your feedback. This exploratory process allows us to deliver features that not only cater to your specific needs, but also seamlessly integrate with our products.
For more insight into GreyNoise Labs and the work we're doing, visit our official website.
The CLI installation process is straightforward:
As an optional step, we recommend installing jq to enhance the readability of CLI output. You can install jq with brew install jq on macOS or apt-get install jq on Ubuntu.
Once installed, you can explore the features of the CLI by running greynoiselabs, which provides a handy usage guide.

Furthermore, you can access command-specific help using greynoiselabs <command> --help.

These commands can help you explore a variety of rich datasets released by GreyNoise Labs. Remember, the data is easily parseable with jq, which can help you extract insights and filter results to suit your specific needs. Some examples of jq usage are provided later on.
jq is a versatile tool for handling JSON data from the command line. Here are a few examples using the JSON outputs above that could provide some interesting insights. Note that these examples are based on the provided samples and may need to be adjusted based on the actual structure and content of your data.
If you wanted to see how many unique C2 IPs exist in your dataset, you could run:
which retrieves all the C2 IPs (.[].c2_ips[]), finds the unique values (unique), and then counts them (length).
If you're interested in the source IPs with high hit counts, you could use a command like:
This filters the data to only include records where the hits are greater than 1000 (select(.hits > 1000)), and then outputs the corresponding source IPs (source_ip).
If you wanted to see how many IPs fall into different categories based on their noise score, you could run:
This command groups the data by the noise score (group_by(.noise_score)), and then transforms it into an array with each object containing the noise score and the count of IPs with that score (map({noise_score: .[0].noise_score, count: length})).
If you wanted to see all popular IPs that are not observed by GreyNoise sensors, you could use:
This command filters the data to only include records where the noise is false (select(.noise == false)), and then outputs the corresponding IPs (ip).
For a glimpse into the distribution of page titles across your network traffic, use.
This command does the following:
By grouping the 'knocks' data based on the title, this updated command allows you to quickly identify which titles have the most associated source IPs. The result is sorted by the ip_count field, giving you an ordered view from most to the least associated IPs for each title.
Finally, with this, you can start to see the power of this data. The first result is a list of IPs likely running Mikrotik routers, that are scanning and crawling the internet and likely related to one or more botnets. Our knockknock dataset has a bunch of granular signature information that could be used to further identify clusters of similar IPs. We will have more on this in a future blog post.
These are just a few examples of what you can do with jq and the new GreyNoise Labs CLI output data. By adjusting these examples to your needs, you can glean a multitude of insights from your data and ours.
As we continue to evolve and expand the functionality of the GreyNoise Labs API and CLI, we are eager to hear your feedback. Your input is critical in helping us understand which features are most valuable and what other capabilities you'd like to see included.
Please don't hesitate to reach out to us with your feedback, questions, or any issues you may encounter at labs@greynoise.io. Alternatively, you can also create an issue directly on our GreyNoise Labs GitHub page. If you have ideas about ways to combine our data into a more useful view or are interested in somehow partnering with a dataset you have, please reach out.
We can't wait to see what you'll discover with the GreyNoise Labs CLI. Get started today and let us know your thoughts!
While our Labs API data is spiffy, you, too, can take advantage of our core data science-fueled threat intelligence platform to identify noise, reduce false positives, and focus on genuine threats. Sign up for GreyNoise Intelligence today and gain the edge in protecting your systems.

All our tags come from extremely talented humans who painstakingly craft detection rules for emergent threats that pass our “100%” test every time. We tend to rely on research partner shared proof-of-concept (PoC) code or vendor/researcher write-ups to determine when we should direct our efforts. Sometimes, prominent, emergent CVEs will cause us to dig into the patch diffs ourselves, fire up vulnerable instances of the software, and determine likely exploit paths which we wait to see are correct.
However, we receive millions of just HTTP/HTTPS events every single day. Deep within that noise we know that exploitation attempts for other services exist, but surfacing ones that may matter is a challenge since we're only human. Thankfully, we also spend some of our time on data science projects that help fuel innovation. You've seen the results of those efforts in our IP Sim and Tag Trends platform features. But, we have many internal data science projects that are designed to give our researchers bionic tagging powers; enabling each of them to be stronger, better, and faster when it comes to identifying novel traffic and understanding whether it is malicious or not (and, whether it warrants a tag).
One of these tools is “Hunter” (yes, the Labs team is quite unimaginative when it comes to internal code names). It performs a daily clustering of HTTP/HTTPS traffic, sifting through those millions of events, and surfaces a very manageable handful of clusters that our dedicated team can easily and quickly triage. Hunter also has a memory of past clusters, so it will only surface “new” ones each day.
Last week was bonkers when it comes to the number of tags (7) our team cranked out.
One reason for that Herculean number is due to Hunter! It led us down the path to finding activity that we might have otherwise only tagged in the future when organizations or agencies announced exploit campaigns that did real harm to those who fell victim to attack.
In the tag round-up for last week, below, we note where Hunter was the source for the creation of the tag with a “🔍”.
The SonicOS TFA Scanner tag identifies IP addresses scanning for the SonicWall SonicOS Two Factor Authentication (TFA) API endpoint. So far, we've observed 503 unique IP addresses from benign scanners searching for this endpoint. For more information and to explore the data, check out the GreyNoise Visualizer for SonicOS TFA Scanner.
This tag is related to IP addresses attempting to exploit CVE-2023-34124, an authentication bypass vulnerability in SonicWall GMS and Analytics. No exploit attempts have been observed so far. For more details, visit the GreyNoise Visualizer entry for SonicWall Auth Bypass Attempt.
We've observed one malicious IP address attempting to exploit CVE-2023-34133, a SonicWall SQL Injection vulnerability. So far, we've seen one IP — 94[.]228[.]169[.]4 poking around for vulnerable instances. — To learn more about this tag and the associated data, have a look at the GreyNoise Visualizer entry for SonicWall SQL Injection Attempt.
This tag is associated with IP addresses scanning for Ivanti MobileIron Configuration Services (MICS). As of now, we haven't seen any IPs attempting to exploit this vulnerability. To dive deeper into this tag, visit the GreyNoise Visualizer for Ivanti MICS Scanning.
IP addresses with this tag have been observed attempting to exploit CVE-2023-38035, an authentication bypass vulnerability in Ivanti Sentry, formerly known as MobileIron Sentry, versions 9.18 and prior. No exploit attempts have been observed to date. Explore this tag further on the GreyNoise Visualizer entry for Ivanti Sentry Auth Bypass Attempt.
IP addresses with this tag have been observed attempting to exploit CVE-2023-32315, a path traversal vulnerability in Openfire's administrative console. We've caught seven IPs attempting to find paths they should not be. You can check those out at the GreyNoise Visualizer entry for Openfire Path Traversal Attempt
Finally, IP addresses with this tag have been observed attempting to exploit CVE-2018-9995, an authentication bypass vulnerability in TBK DVR4104 and DVR4216 devices. Looking back at the past 30 days of data, we found 66 IPs looking for these streaming systems. You can find them all at the GreyNoise Visualizer entry for TBK Vision DVR Auth Bypass
The earlier we can find and tag new, malicious activity, the more quickly our customers and community members can take advantage of our timely threat intelligence to either buy time to patch systems and block malicious activity.
You, too, can take advantage of our data science-fueled threat intelligence platform to identify noise, reduce false positives, and focus on genuine threats. Sign up for GreyNoise Intelligence today and gain the edge in protecting your systems.
Do you have a tag that you want GreyNoise to look into? You are in luck! We now have a page for our Community to request a tag. Check it out.

Many traditional threat intelligence solutions used by MSSPs can have an unintended consequence of creating more noise for your security operations center (SOC) – GreyNoise changes that. We collect and analyze internet wide scan and attack traffic, and label noisy IPs and network activity (whether it's common business services, or scanners crawling/exploiting the internet) to help SOC teams spend less time on irrelevant or harmless activity, and more time on targeted and emerging threats.
GreyNoise integrates seamlessly into over 50 different security tools, eliminating the need for security professionals to adapt to new dashboards, switch between multiple platforms, or navigate additional graphical user interfaces. This enables MSSPs to materially improve their security operations and workflows, often saving them hours of analyst time per week and upwards of 25% on costs.
In our last post, we introduced three critical ways MSSP and MDR customers benefit from GreyNoise: 1) reduce costs 2) improve scalability and 3) beat the adversary.
In this post, we will take a deeper look at exactly HOW existing GreyNoise MSSP customers are realizing these benefits.
As threat landscapes evolve, so does the cost of staying ahead. More security alerts often result in a need for more headcount, and when MSSPs are already operating on narrow margins – this becomes quite the challenge.
Over at Ideal Integrations, a well-known regional MSSP, they faced two costly challenges:
By integrating GreyNoise into Swimlane, their Security Orchestration, Automation & Response platform (SOAR), the Ideal Integrations team was now able to take each alert, ask GreyNoise (via API) for a temperature check on that IP Address, and immediately enrich it with GreyNoise-provided context – enabling a trusted, reliable verdict quickly. With the decision and reasoning directly available in their alert systems, the analysts no longer needed to bounce between different platforms to collate results, streamlining the incident response process.
In today's market, scaling is not enough. For MSSPs in particular, it is all about scaling sustainably – growing your customer base without increasing your costs.
Hurricane Labs, a leading Splunk MSSP shop, had brought together a team of Splunk ninjas who were second-to-none in managing the Enterprise Security and Phantom deployments on behalf of their customers. However, as they added more detections and new customers, they naturally saw their alert volumes grow.
To enrich and filter out noisy alerts in both Splunk and Phantom, Hurricane Labs installed the GreyNoise integration into their customers’ Splunk environments and added it to the workflows for various detections. The logic was straightforward: if something in the search results matched GreyNoise, exclude.
For a normal enterprise business, the SOC manager has a couple of choices to handle alerts: he or she can hire a person, or spend money on a product that improves alert quality. But for an MSSP, the margins are often paper thin – and that’s where GreyNoise is even more valuable.
The adversary is evolving its tactics and techniques faster than ever, making it critical for MSSPs and MDRs to have sufficient tooling and insights to stay ahead. One part of this equation is the need for explainability and context paired with threat intelligence, and the other is visibility into emerging vulnerabilities and associated attack vectors – especially with “vulnerability exploit” now cited as a top attack vector (Verizon DBIR).
MSSPs like Layer 3 Communications & Ideal Integrations leverage GreyNoise data to help them prioritize threats and vulnerabilities based on the absence or presence of “in the wild” exploitation. During the height of vulnerability events, GreyNoise also serves critical in providing customers with the “most comprehensive set of intelligence” through high fidelity blocklists. Organizations can prevent noisy scanners from hitting their perimeter from the onset, effectively shutting them out, and giving themselves time to patch when there is an emerging exploit. This allows GreyNoise MSSP and MDR customers to tighten the window of opportunity for attackers and ultimately improve the overall security posture of their end clients.
With a unique suite of tools and insights, GreyNoise is truly an opportunity for every MSSP and MDR to transform their offerings with a threat intelligence solution that pays for itself.
That is why we are excited to invite you to our upcoming webinar, "Alerts, Automation, & Analysts: How MSSPs Can Leverage Automation to Reduce Alerts & Maximize their Analysts." This webinar will feature an expert panel of MSSP & MDR leaders from real GreyNoise customers, providing valuable insights and strategies.
Don't miss out on this opportunity to learn from industry experts real-time, and see how GreyNoise is shaping the future of sustainable, scalable and innovative cybersecurity service delivery.


The GreyNoise Labs team is proud to have hosted the GreyNoise NoiseFest 2023 CTF - who knows if we will do it again, but we had fun, so here’s a walkthrough on how and why we did it.
We’re incredibly proud of everybody who even attempted to play - all 280 participants! Our community team has contacted the winners, and they will be receiving some sweet swag as a prize, plus 1st, 2nd, and 3rd places are getting a beautiful trophy.

Crafting the CTF was one of the best parts of hosting the competition. Competitors in the CTF may have noticed that there was no usage of GreyNoise - and that was by design. When we thought about all the cool things we do daily on the Labs team, we narrowed it down to around 25 tags with CVEs that have led us down rabbit holes or taught us something interesting about how the internet works.

We used these selected examples and packaged them in industry standard PCAP format and set our community loose on the CTF challenges. This allowed us to observe the methods, tools, and pain points in dealing with network traffic that may defy typical expectations. We know that this format of network capture is the highest level of proof that something occurred - the direct record of bytes on the wire. A detection engineer is not only familiar with PCAP but may even live in it daily, noticing how bytes live and breathe just as the GreyNoise Labs team does.
Our new sensor fleet also captures full PCAP, and we wanted to hype that fact! Any difficulties encountered with a single-packet CTF challenge will be grossly exacerbated when working with millions of real-world packets. We’re greatly looking forward to analyzing the pain points from this CTF and providing the tooling that our Detection Labs team and the community need to make network analysis a pleasure to work with. Your feedback has been heard!
So we learned some things about hosting a CTF - mainly that creating “medium level” challenges in a PCAP-based CTF is hard. We also learned that we like trivia - the challenge “fullsignature” is an excellent example of this, where the answer was the name of the patent holder and original author for the MSMQ protocol. Most importantly, we learned that our community is SUPER SMART in PCAP. Some of the players have done writeups already (this one by An00bRektn, or this one by t3mp3st), and if you’d like to walk through the challenges yourself, we’ve uploaded the challenges and associated PCAP to GitHub at https://github.com/GreyNoise-Intelligence/NoiseFest-CTF-2023/
Altogether, we learned a lot from this experience and had a great time crafting and solving each other’s challenges here on the GreyNoise Labs team. We look forward to hosting again!

Cybersecurity digerati spends an inordinate amount of time focusing on the concept of “biggest” when it comes to cybersecurity threats. While there is some merit to such quantification, the concept itself can be difficult to generalize, since every organization has some set of unique characteristics that cause each of them to have fairly unique threat profiles, risk tolerances, and exposures.
We can, however, break down some of the broader themes from Black Hat and DEF CON 2023 and pull out some recurring themes across each that would cause some consternation for CISOs, CIOs, CEOs, and board members (since many of them are now on the hook when cyber things go south).
Meltdown, Spectre, and L1 Terminal Fault (Foreshadow) may be behind us, but modern processor architectures seem to be in a permanent state of vulnerability. Downfall is yet another one in this line of low-level flaws that require significant effort to mitigate, as said mitigations usually require some downtime and also some inherent risk in the patch processes themselves.
Fixing these vulnerabilities also may cause significant performance degradation, which may force organizations to incur extra spend to meet pre-projected capacity requirements.
C-suite folks are left with a gnarly, tangled risk assessment process that has to consider the likelihood and frequency of projected attacks and also the potential impact on various compliance requirements if they choose not to patch/mitigate.
This is a major distraction from delivering on core business functions, and we’re likely to see more of these types of vulnerabilities in the future, especially with the scramble to acquire GPUs. CVE-2022-31606, CVE-2021-1074, and CVE-2021-1118 are already known vulnerabilities in GPUs, and the rush to meet AI headfirst may see a parallel set of headaches on the horizon in any systems that are performing advanced ML/AI processing.
It’s no secret that an ever-increasing number of organizations are moving some or many workflows to cloud environments, joining the ranks who have blazed the trail before them. There was supposed to be some inherent level of trust in cloud providers to take security seriously, so all an organization had to do was ensure they didn’t mess up their configs or expose vulnerable services. Sadly, that has not been the case for some time now.
The specifics of what were presented at or before Hacker Summer Camp in this space really aren’t as important as the theme itself: you can no longer even remotely have any baseline level of assurance that the cloud environments you are adopting are taking security measures seriously.
This puts C-suite folks in a precarious position. While some cloud plans end up going over budget, there are many cloud use cases that do help organizations save time, money, and people resources. Yet, when you are put at serious risk due to negligence on the part of a cloud provider you have the potential of incurring significant costs for triage, incident response, and potentially data breach penalties.
2023 has made it pretty clear that “In Cloud, We Trust” is unlikely to ever be a motto again (if it ever was). Organizations now have extra complexity both up-front (as they bake in extra security measures and potential incident costs into new endeavors) and also as they handle the distraction of retrofitting a more defensive security posture onto systems that were likely more secure when they were hosted back in the “owned data center” days.
There has been enough discussion about “AI insecurity” ever since just around this time last year, so I can keep this relatively brief.
The large language/generative models (LLM/GPTs) we seem to be stuck working with were all trained with no thought for safety — either in the results one gets when using them, or for how easy it is to cause them to reveal information they shouldn’t.
They also come with an equivalent to the “cloud” problem mentioned above, since most organizations lack the skill and resources necessary to bring AI fully in-house.
This is a big topic of discussion when I talk to CISOs in my lectures at CMU. The AI gold rush is causing organizations to incur significant, real risk, and there are almost no tools, processes, guides, or bulk expertise to help teams figure out ways to keep their data, systems, and humans safe from AI exposures.
This is yet one more distraction, and focus grabber that makes it very difficult to just get “normal” cybersecurity practices done. Unless the bottom falls out of generative AI as it has with the web3/crypto fad that came before it, the C-suite will have to dedicate what little time and resources they have to corralling and shaping AI use across the organization.
There were many talks about vulnerabilities in general at both Hacker Summer Camp and RSA this year. But, I don’t think any talk made the brutal reality of what it is like to perform the thankless task of vulnerability management within even a moderately sized organization.

That calendar view has a colored square every time there’s been a CISA Known Exploited Vulnerability release since CISA began curating their catalog. Apart from the regular mega “Patch Tuesday” organizations have to deal with, they also have to contend with nigh immediate response to each new update, even if that’s only a triage event. There is little time in-between updates, and very common technologies/products make their way to the list on-the-regular.
Six weeks before Black Hat, there was at least one, major vulnerability in a core component of most enterprise IT stacks every week, with rapid and devastating malicious attacks following close behind each release.
This is an untenable situation for most organizations, even “resource rich” ones.
Hundreds (one estimate, today, said “thousands”) of organizations have been devastatingly hurt by MOVEit exploits, Citrix admins likely cannot sleep at night anymore, and even security teams have had to face an onslaught of patches for technology they’re supposed to be using to keep their organizations safe.
We rarely talk about this because it’s a hard problem to solve and causes real, lasting damage. It’s far “cooler” to talk about that “EPIC vulnerability” some clever researcher found in isolation. But, when they’re disclosed back-to-back, as a few security vendors did before Black Hat, it quickly moves from “cool” to a cold, hard annoyance.
More work needs to be done at and outside Summer Camp to help figure out ways to enable defenders to keep their own shops safe without dealing with the IT equivalent of a weekly hurricane sweeping across their asset landscapes.
“Recurring theme” is just a fancy way of saying we’re repeating the same negative patterns of the past and making little to no headway, or — to put it another way — we’re in a “two steps forward; three steps back” operational model as we work to overcome each new challenge.
However, all is not doom and gloom, and there are ways to strive for more positive outcomes.
Fundamentally, organizations must take a proactive and pragmatic approach to enhance their security posture.
For CPU vulnerabilities, investigate tools that can help detect and mitigate risks, and have a plan to rapidly patch and potentially downgrade performance if needed. Cloud providers should be evaluated closely, with redundancy and controls to limit damage from potential exposure. AI and generative models require robust testing, monitoring, and human oversight to prevent harmful outcomes.
Most crucially, vulnerability management programs require sufficient staffing, automation, and executive buy-in. Prioritization aligned to business risk can help focus limited resources. Communication and collaboration with vendors, regulators, and peer organizations could also move the needle on systemic issues.
While hacker conventions highlight scary scenarios, security leaders who take balanced action can still fulfill their mission to protect their organizations. With vision, realism, and tenacity, progress is possible even in the face of ongoing challenges.
Remember, GreyNoise has your back when it comes to vulnerability intelligence. We’re here to help you keep up with the latest CVEs, assist you in triaging a barrage of IoC’s, or providing you with the essential details necessary to make sense of the ever-changing vulnerability landscape.

The Managed Security Service Provider (MSSP) and Managed Detection and Response (MDR) markets continue to face significant challenges in handling a large number of security alerts and vulnerabilities across multiple client environments. While this task is made even more difficult by the shortage of cybersecurity professionals in our industry, it is critical to note that the ideal solution isn’t adding more hands on deck. It's leveraging innovation and technology that amplifies the capabilities of existing teams.
MSSPs & MDRs require solutions that enable them to provide top-notch services to their clients while balancing already thin profit margins, all while ensuring they prevent analyst burnout. They need ways to quickly identify and respond to threats with confidence, without compromising on efficiency or service quality.
At GreyNoise, we understand the importance of every second in your margin-driven business. That's why we save you time, resources, and money – all while helping you expand your customer base. We gather, analyze, and categorize data on IPs that mass scan the internet and saturate security tools with noise. This allows analysts to spend less time on irrelevant or harmless activity and more time on targeted and emerging threats.
Here are just a few of the ways GreyNoise is helping our MSSP & MDR customers:
GreyNoise scales in a way your analysts can’t. But don’t just hear it from us – see how leading MSSP Hurricane Labs is reducing costs while growing their customer base with GreyNoise.
"Any single analyst can handle, say, 20 alerts per day. But a product like GreyNoise can triage alerts for every one of our customers. So as we add more customers, GreyNoise scales in a way a person can’t.”
-Director of Managed Services, Hurricane Labs
Want to learn more about how GreyNoise can help your MSSP & MDR? Schedule a demo with a GreyNoise expert.

As we roll through the summer, GreyNoise is back from its July two-week shutdown with a bunch of fresh new improvements, including 63 new tags and a bunch of exciting new data insights for our customers to explore in our Labs API. We’ve also updated our integrations to add support for our IP Similarity and Timeline for our Palo Alto customers.
We’re excited to announce the availability of our Labs API. The Labs Beta API is a data source derived from the GreyNoise sensors and platform specifically designed to uncover insights our users may find intriguing and to facilitate exciting data explorations related to emerging threats. These APIs are in beta today; however we welcome feedback that will improve the quality of our data and suggestions on how we can add them to our product. Here are some of the datasets you can explore today:
Access the top 10% of possible Command and Control (C2) IP addresses, ranked by their pervasiveness, observed by GreyNoise over the previous 24 hours. Use this query to identify second-stage IP addresses that might be involved in malicious activities following the reconnaissance and initial access stages.
Access the top 1% of HTTP requests, ranked by their pervasiveness, observed by GreyNoise over the last seven days. Gain insights into the background radiation of the internet, exploring the patterns and trends of HTTP requests.
Access the top 1% of IPs searched in GreyNoise, ordered by the number of users observed searching over the last 7 days. Understand commonalities in how users search within GreyNoise, gaining insights into popular IPs and their associated activities. This query uses a minimum number of IP submissions and users to build consensus before an IP can be considered available in this dataset.
Access the top 1% of IPs by their noise score for the last 7 days. This score is determined by comparing the pervasiveness of the number of sensors and countries that observed packets from the IP, the request rate, and the diversity of payloads and ports for which the packets were observed. This query is intended to help rank the top noise makers compared to the quiet single-hit scanners.
We’ve added a “Create Alert” button in the Action panel on the Tag details page to make it easy to create an alert. GreyNoise users can use this to monitor scanning activity directly from the Tags page, informing them of any new IPs scanning for tags they are interested in.
There is now a Copy/Search button in fields on the IP details page. The previous behavior did not allow users to copy the values in the fields.

You can access the Copy/Search buttons by hovering over fields such as Ports Scanned, Country, OS in the IP Details pages.
Previously, the Analysis Feature only accepted inputs up to 2MB. We've increased this to 4MB, so that customers can submit larger files without getting an error.

We updated our Palo Alto XSOAR support to include our IP Similarity and IP Timeline features, allowing users to easily find similar IP addresses, or review GreyNoise’s classification history on an IP.


To learn more about using the XSOAR Demisto enhancements for IP Similarity and Timeline, you can check out our documentation.
In June & July, GreyNoise added 63 new tags:
56 malicious activity tags
2 benign actor tags
5 unknown tags
All GreyNoise users can monitor scanning activity we’ve seen for a tag by creating an alert informing them of any new IPs scanning for tags they are interested in.
Don't have a GreyNoise account? Sign-up for free.

(See below for the most recent update: 2023-08-03)
Citrix recently disclosed a single critical remote code execution (RCE) vulnerability, CVE-2023-3519, affecting NetScaler ADC and NetScaler Gateway (now known as Citrix ADC and Citrix Gateway. This vulnerability has a CVSS score of 9.8, making it a high-risk issue.
GreyNoise has a tag — Citrix ADC/NetScaler CVE-2023-3519 RCE Attempt — that organizations can use to proactively defend against sources of known exploitation.

Over the past several days, numerous organizations have contributed their pieces of the puzzle, both publicly and privately. While the most recent Citrix Security Advisory identifies CVE-2023-3519 as the only vulnerability resulting in unauthenticated remote code execution, there are at least two vulnerabilities that were patched during the most recent version upgrade.
Through the analysis by Rapid 7 and AssetNote a memory corruption vulnerability was discovered in the ns_aaa_saml_parse_authn_request function that handles Security Assertion Markup Language (SAML), which can be reached through HTTP POST requests to “/saml/login”. This vulnerability has been demonstrated to corrupt memory and cause program crashes, but it is unknown whether it can be leveraged for remote code execution at this time.
Through the analysis by Bishop Fox’s Capabilities Development team together with GreyNoise a memory corruption vulnerability was identified in the ns_aaa_gwtest_get_event_and_target_names function. This function can be reached through HTTP GET requests to “/gwtest/formssso”. This vulnerability was demonstrated as capable of being leveraged for stack corruption, leading to remote code execution; and, was further corroborated by AssetNote’s Part 2 Analysis.
Through analysis from Mandiant some indications of compromise (IoCs) and post-exploitation activity are now known. As part of their provided IoCs they shared that an HTTP POST request was used in initial exploitation as well as HTTP payloads containing “pwd;pwd;pwd;pwd;pwd;” which may be useful for writing detection signatures.
On July 28th GreyNoise began observing activity — https://viz.greynoise.io/tag/citrix-adc-netscaler-cve-2023-3519-rce-attempt?days=30 — for CVE-2023-3519 wherein the attacker was attempting to leverage the vulnerability for memory corruption. An initial analysis of the observed payloads indicates that the attacker initially sends a payload containing 262 `A`'s which would result in a crash of the Citrix Netscaler `nsppe` program. They follow up with two variants using URL Encoded values and appear to be attempting to remotely execute the command `/bin/sh -c reboot` which would result in a full reboot in the system. However, it appears that the attacker may not be aware of the CPU endianness of vulnerable systems. The payloads they are attempting to send would result in memory corruption, but would not result in remote code execution as they expected. This would result in the `nsppe` program crashing.
The observed payloads are provided below for completeness.
Please update your search term or select a different category and try again.