Is it really cRiTiCaL?
You don't have time to worry about unexploited vulnerabilities.
Get real-time insight into active exploitation to truly understand criticality.
Overview
As CVE counts grow, many organizations accept unpatched risks—until exploits go public and mass exploitation begins. When that happens, every minute counts.
GreyNoise helps you focus on actively exploited vulnerabilities. Unlike static severity and probability scores, GreyNoise supplies real-time, primary-sourced intelligence on attacks we see in-the-wild.
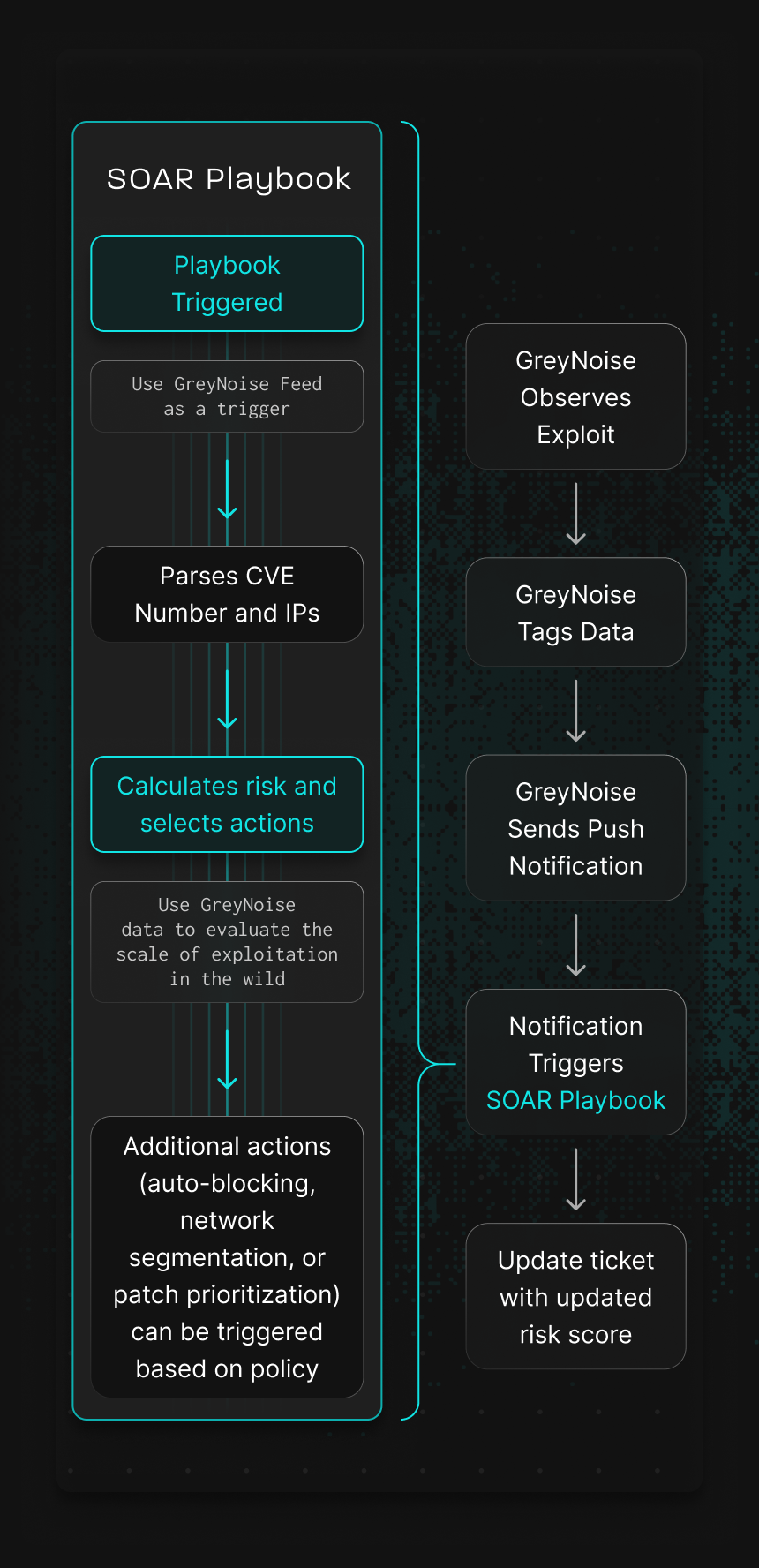
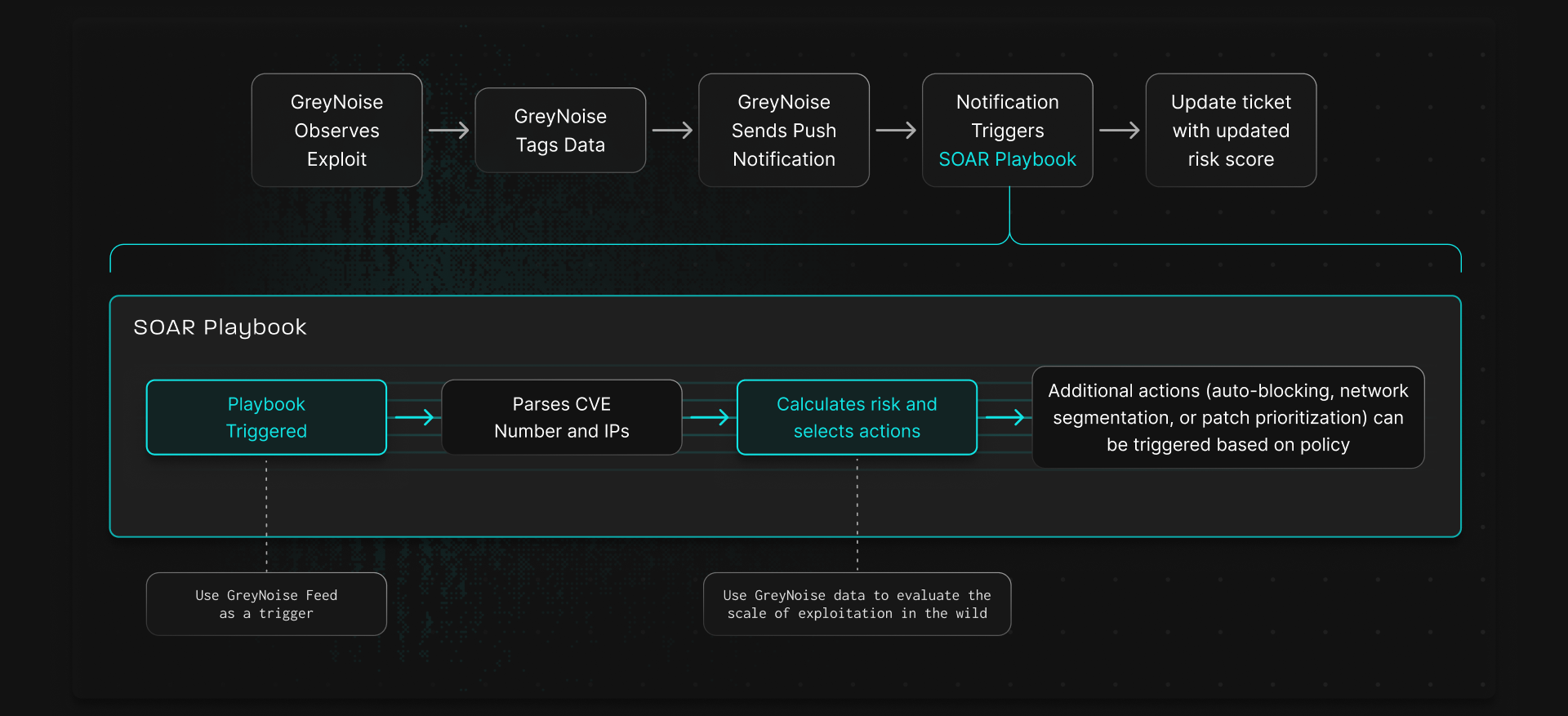
How GreyNoise Helps You
Prioritize the Most Urgent Vulnerabilities
Prioritize Exploited Vulnerabilities
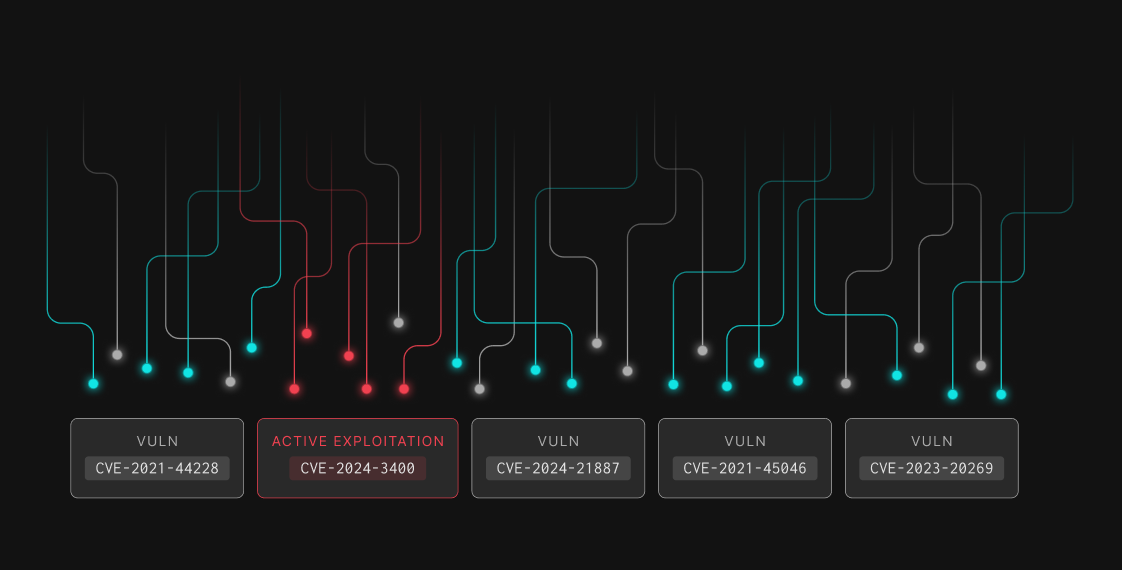
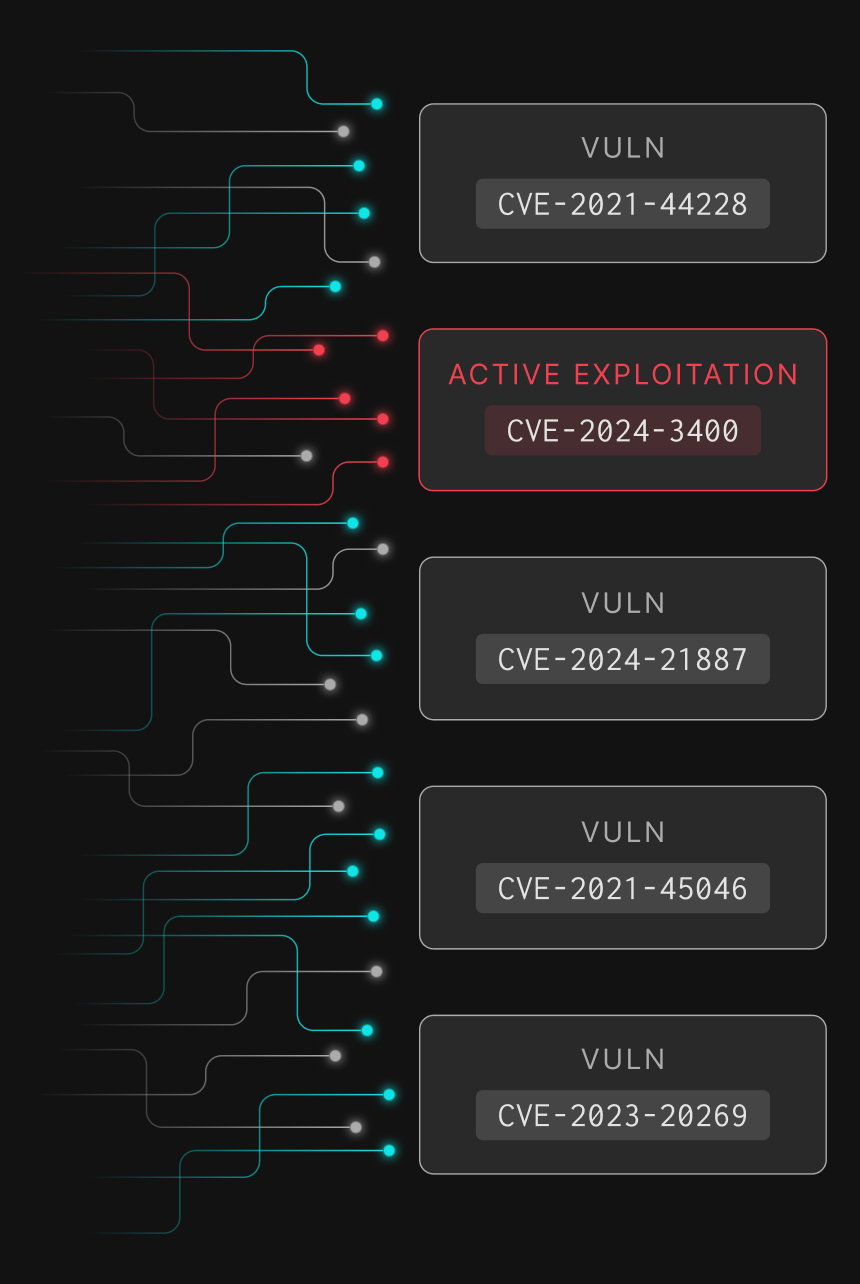
GreyNoise highlights CVEs actively scanned or exploited, helping teams focus on real attacker activity—not theoretical risk.
Reduce Patch Fatigue
By filtering out untargeted CVEs, GreyNoise lets teams focus resources on vulnerabilities that matter most.
Validate Threat Exposure
Teams can match GreyNoise data to their assets to confirm which exploits truly affect them.
Data-Driven Patching
Linking remediation urgency to live threat activity helps justify priorities and prove data-driven patch management.
IP Blocking as Mitigation
Use GreyNoise query-based, dynamic IP blocklists for emergency mitigation as you implement longer-term fixes.
How it Works